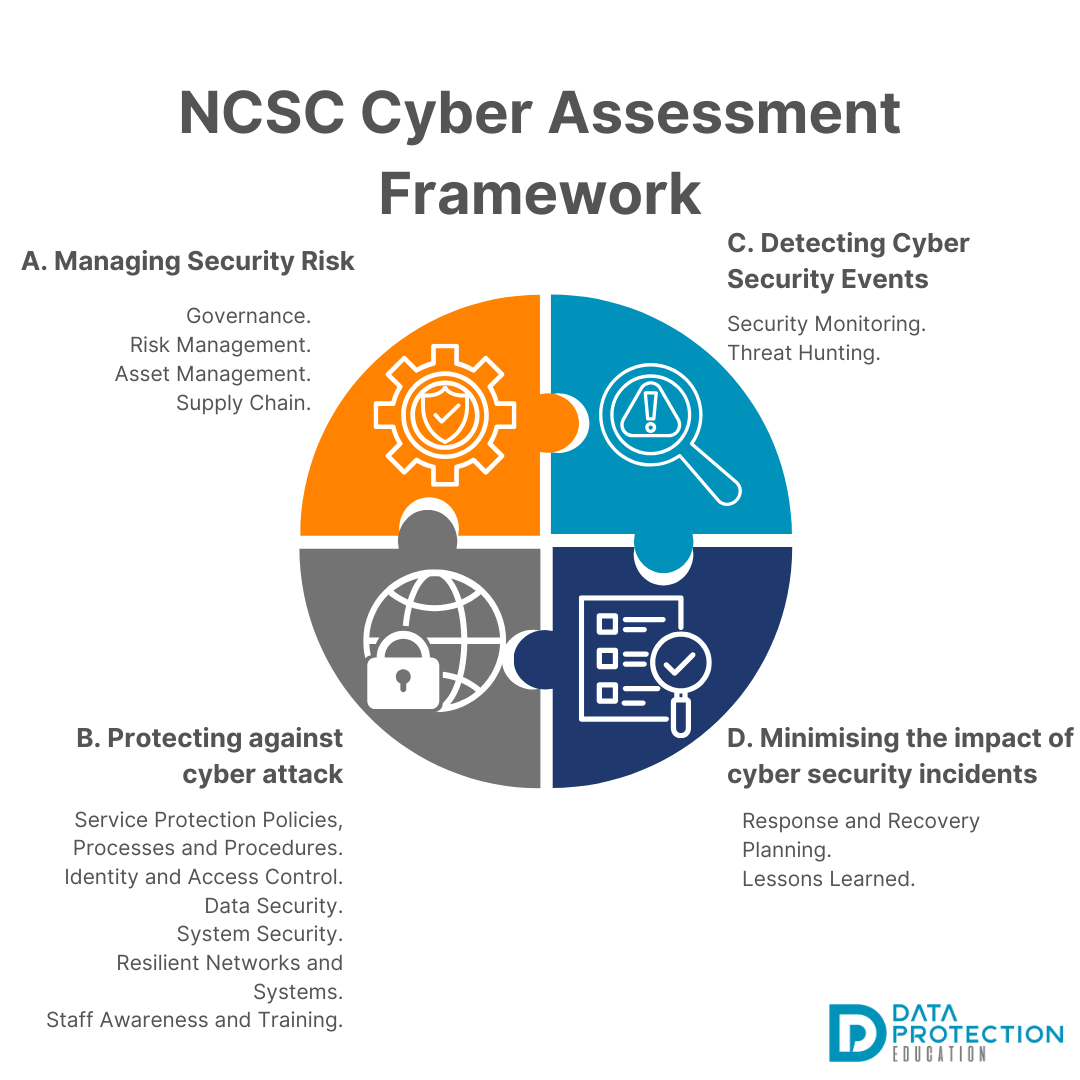
The NCSC Cyber Assessment Framework
The Cyber Assessment Framework (CAF) is cyber security guidance for organisations that play a vital role in the day-today life in the UK and organisations should look to it as guidelines for helping keep data safe.
The CAF is a tool to help organisations assess and improve their cyber security and resilience, managing cyber risks and protecting essential services from cyber threats.
The CAF is primarily designed for organisations operating essential services, in sectors such as energy, healthcare, transport, digital infrastructure and government - this includes schools and colleges.
The CAF collection is for all organisations that are responsible for securing critical network and information systems that keep our businesses, citizens and public services protected.
The CAF collection is aimed at helping an organisation achieve and demonstrate an appropriate level of cyber resilience in relation to certain specified essential functions performed by that organisation.
Schools and colleges should note that the CAF will help them reach the DfE Digital Standards requirements as the categories are closely linked:
-
Objective A - Managing Security Risk
- Governance
- Board Direction
- regular board level discussions
- board level representative
- board direction translated into organisational practices
- security is recognised as an important enabler
- Roles and Responsibilities
- key roles and responsibilities for network and information security have been defined
- clarity about who has overall accountability for the security of the network and information systems
- Decision Making
- senor management have visibility of key risk decisions made
- risk management decision-making is delegated and escalated where necessary
- risk management decisions are regularly review
- Board Direction
- Risk Management
- Risk Management Process
- risks to network and information systems are identified, analysed, prioritised and managed
- your approach to risk is focused on the possibility of adverse impact on your essential function (s).
- your risk assessments are based on clearly understood set of threats assumptions
- your risk assessments are dynamic and readily updated
- your risk management process is regularly reviewed for effectiveness
- you anticipate technological developments that could be used to adversely impact network and information systems
- Understanding Threat
- you perform detailed threat analysis
- you include methods and techniques available to threat actors to understand how they could be used against you
- you understand the steps a threat actor would take to reach a probable target
- you understand what measures can be used to reduce the likelihood of the threat actor reaching the target
- you maintain a list of current threats and apply it to your risk management decision making
- you document steps required to undertake a threat analysis
- Assurance
- you validate security measures in place
- you can justify your validations and confidence
- security deficiencies are addressed
- Risk Management Process
- Asset Management
- Asset Management
- all assets are identified and documented
- dependencies are documented and records
- assets are prioritised
- responsibility is assigned for asset management
- assets are managed with cyber security in mind
- Asset Management
- Supply Chain
- Supply Chain
- you understand your supply chain
- you understand who your suppliers sub-contract to
- you consider the risks to the wider network
- critical suppliers can demonstrate appropriate levels of cyber security
- you understand which contracts are relevant
- third party data sharing is managed
- in the event of an incident, your suppliers provide mutual support
- Secure Software Development and Support
- your software suppliers leverage a secure software development framework
- the supplier understand the software and any third-party components
- the security of the software is considered
- the software is has integrity and is updated and patched
- Supply Chain
- Governance
-
Objective B - Protecting against cyber attack
- Service Protection Policies, Processes and Procedures
- Policy, Process and Procedure Development
- you fully document your overarching security governance and risk management approach
- cyber security is integrated and embedded
- your policies are practical and usable
- policies, processes and procedures are updated regularly
- threats trigger reviews when the essential functions are threatened
- systems are secure even when users might not follow processes
- Policy, Process and Procedure Implementation
- your policies, procedures and processes are followed
- and integrated with other organisational policies such as HR assessments
- policies, processes and procedures are communicated effectively
- approached action is taken to address breaches of policy
- Policy, Process and Procedure Development
- Identity and Access Control
- Identity Verification, Authentication and Authorisation
- initial identity process is robust
- only authorised and authenticated users can access your essential functions
- authorised users are limited to what is necessary
- additional authentication is used such as MFA for all users
- user lists are reviewed at least every six months
- you follow user authentication best practice
- Device Management
- only trusted devices can perform privileged operations
- you obtain assurance when any third-parties connect to your network
- certificated based device identity is used
- regular scans of devices are performed
- Privileged User Management
- privileged accounts are separate and closely managed, and reviewed
- temporary accounts with time-bound rights for external third parties is in place
- Identity and Access Management
- there is a robust procedure to identify and verify every user
- user access rights are reviewed (leavers and joiners processes)
- all access is logged
- logs are reviewed
- unauthorised access attempts are alerted, assessed and investigated
- Identity Verification, Authentication and Authorisation
- Data Security
- Understanding Data
- you have identified and catalogued all the data important to the operation of your network and supporting your essential functions that would assist a threat actor
- you document who has access to the data
- there is an understanding of the location, quantity and quality of data
- unnecessary copies are removed and you only keep what you need (data minimisation)
- all mobile devices and media that hold data are identified
- data links to transfer data are identified
- dependencies of your important data are understood
- impact to essential functions of data breaches is documented
- Data in Transit
- all data links to transfer data are identified
- appropriate physical and/or technical means are applied
- suitable transmission paths are available
- Stored Data
- copies of important data are provided with limitations and as a read only
- data is stored with appropriate technical means
- there are suitable and secure backups of data
- historic or archive data is suitably stored
- Mobile Data
- mobile devices are catalogued and centrally controlled
- mobile devices can be remotely wiped
- data is minimised on mobile devices and may be automatically deleted after a certain time period
- Media/Equipment Sanitisation
- you devices with important data are tracked
- data is removed from all media before reuse or disposal
- Understanding Data
- System Security
- Secure by Design
- you employ appropriate expertise for your network
- the network is segregated
- there are simple data flows across networks
- the network is designed to be easy to recover
- there are appropriate restrictions for automated decision making
- Secure Configuration
- security configurations are documented and managed (i.e. patching, updating)
- you have a baseline configuration
- changes are managed
- the network is regularly reviewed
- only permitted software can be installed
- automated decision making is understood and decisions can be replicated
- generic and default accounts are removed
- Secure Management
- only authorised, privileged users from highly trusted devices can administer the network/essential functions
- information about network and information systems is regularly reviewed and updated
- you prevent, detect and remove malware
- Vulnerability Management
- exposure of essential systems to publicly known vulnerabilities is understood
- known vulnerabilities about your systems are tracked
- testing is regularly performed to understand vulnerabilities of the information systems and network
- the use of supported software, firmware and hardware is maximised
- Secure by Design
- Resilient Networks and Systems
- Resilience Preparation
- you have business continuity and disaster recovery plans
- you use sources to identify new levels of risk and threats
- Design by Resilience
- key areas of the network (essential functions) are segregated
- email and internet are not available from network and information systems supporting your essential functions
- resource limitations are mitigated
- geographical constraints are mitigated
- all the above are reviewed and updated
- Backups
- backups are secured at centrally accessible secondary sites
- backups of important data are made, tested, documented and routinely reviewed
- Resilience Preparation
- Staff Awareness and Training
- Cyber Security Culture
- your executive management clearly communicates cyber security priorities to all staff, including positive cyber security attitudes, behaviours and expectations
- anyone raising a potential cyber incident is treated positively
- everyone is recognised for their contribution
- management is actively involved and committed
- your organisation is open about cyber security and concerns are taken seriously
- the organisation collaborates about cyber security
- Cyber Security Training
- all staff members follow appropriate cyber security training paths
- all training is tracked and refreshed
- your cyber security training is regularly reviewed
- cyber security information and good practice is easily accessible
- Cyber Security Culture
- Service Protection Policies, Processes and Procedures
-
Objective C - Detecting Cyber Security Events
- Security Monitoring
- Sources and Tools for Logging and Monitoring
- monitoring is based on a thorough understanding of the network
- your monitoring data is detailed enough to detect security events and support investigation
- there is extensive monitoring of user and system activity
- there is host-based monitoring
- anything relating to your essential functions are considered potential logging and monitoring data sources
- log data sets are synchronised
- log data is enriched with other network data
- data sources and tools are regularly reviewed
- it is possible to pinpoint activity
- Securing Logs
- access to log data is limited
- logging architecture can protect itself from threats
- analysis and normalisation is performed on copies of log data
- all actions involving log data can be traced
- integrity of log data is protected
- Generating Alerts
- indicators of compromised are easily detected
- all updates and new signatures are promptly applied
- security alerts supporting essential functions are priorities
- security alerts are enriched with
- alerts and detections are reviewed and tested regularly
- alerts are customisable (although they may used off the shelf tooling rules)
- you continuously monitor for abnormalities
- real time logging
- Triage of Security Alerts
- you investigate and triage alerts; you also document
- there are playbooks covering all plausible use cases
- you prioritise after triage
- you understand normal user and system behaviour to effectively triage
- Personnel Skills for Monitoring and Detection
- there are monitoring and detection personnel
- they have defined roles
- they follow policies, processes and procedures
- they are empowered to look beyond the fixed process and investigate
- they are ware of your essential functions, information systems and related assets
- they drive and shape new data log collection
- they follow all of the required workflows
- they have sufficient understanding of the operational context
- they deal with their workload effectively
- Understanding User's and System's Behaviour, and Threat Intelligence (within Security Monitoring)
- you track the effectiveness of your threat intelligence
- you use risk-based and threat-informed decisions to select threat intelligence feeds
- threat intelligence is available to the necessary users
- threat intelligence is contextualised
- you understand normal user and system abnormalities
- you monitor for adverse activities likely to impact network and information systems
- you are regularly updated to reflect changes in network and information systems
- you possess the capability to share threat intelligence
- Sources and Tools for Logging and Monitoring
- Threat Hunting
- Threat Hunting
- you understand the resources required
- your deployment matches the risk
- your threat hunts follow pre-determined and documented methods
- when appropriate threat hunts are automated
- details of threat hunts are recorded and used to drive improvements
- you have justified confidents in the effectiveness of your threat hunts Your threat hunts focus on the tactics, techniques and procedures (TTPs) of threats over atomic IoCs
- Threat Hunting
- Security Monitoring
-
Objective D - Minimising the impact of cyber security incidents
- Response and Recovery Planning
- Response Plan
- your incident response plan is based on a clear understanding of the security risks
- it is comprehensive and covers likely impacts
- your incident response plan is documented and integrated with the organisation's wider business
- it is communicated and understood
- Response and Recovery Capability
- you understand the resources required
- you know what types of information will be needed to inform response decisions; there are arrangement in place to make this information available
- your response team has the skills to decide on action to limit harm and have the authority to carry them out
- operational delivery knowledge is shared with everyone involved
- Backup mechanisms are available
- arrangements exist to augment your incident response plan
- Testing and Exercising
- exercise scenarios are based on incidents experience
- they are documented and regularly reviewed
- exercises are regularly run and are used to refine plans
- exercises test all parts of the response cycle
- Response Plan
- Lessons Learned
- Post Incident Analysis
- is conducted routinely
- your post analysis is comprehensive
- relevant incident data is made available to the analysis team
- you consider what could have happened under alternative scenarios
- Using Incidents to Drive Improvements
- there is a documented incident review process
- lessons learned cover processes, procedures and technical aspects of systems
- they are used to improve security
- security improvements are prioritised
- analysis is fed to senior management
- lessons learned are maximised using the what if analysis
- you learn from reported incidents in your sector and the wider national infrastructure
- Post Incident Analysis
- Response and Recovery Planning
This is a summary of the criteria, sections may be 'achieved', 'partially achieved' and 'achieved' apart from the Response and Recover and Lessons Learned which are either 'achieved' or 'not achieved.
The full framework can be viewed: NCSC Cyber Assessment Framework
We've created an overview of the framework: