Data Protection Competency Framework
Data Protection Education is pleased to issue this Data Protection Competency Framework.
We commissioned this work from Miss IG Geek because we wanted another set of eyes on an important, but seemingly missing piece of the data protection jigsaw - that is the human element.
We often hear our colleagues, customers and ourselves say that "people are the biggest risk" and we see this daily - systems security in place, but defences and data breached through human error or deception. But the human factor goes beyond the risk of a phishing attack - it's about roles throughout the organisation.
In data protection law the organisation has accountability, but organisations are made of people. Therefore, ensuring that your people understand their role and what it requires of them to ensure the organisation as a whole has an effective data protection programme is key. It isn't simply the role of the IT department or the office administrator - everyone has a role.
That's why this framework is so valuable - it's not just a set of skills and attainments. Rather, it looks at what different roles exist in data processing and assigns the competency to that role, understanding that in different processing activity, people may be doing different things.
We commissioned this work because we wanted to map roles effectively in our record of processing activity tool and when conducting data protection impact assessments. This framework allows us to provide staff with a personalised report and learning plan based on what they actually do. After all, if people are the biggest risk, we have to put them at the heart of the data protection risk management framework.
We've made this data protection competency framework available under a creative commons licence because we want you to use it, benefit from it and develop it for your needs.
We'd love to hear from you about how you use and adapt it in your organisation and industry. That means send us your ideas, suggestions for improvement and any adaptations that you make - we really want to see this grow across the community.
James England
Director
Data Protection Education Ltd.
We don't require your information or registration to access these resources.
Keep in touch
What's inside?
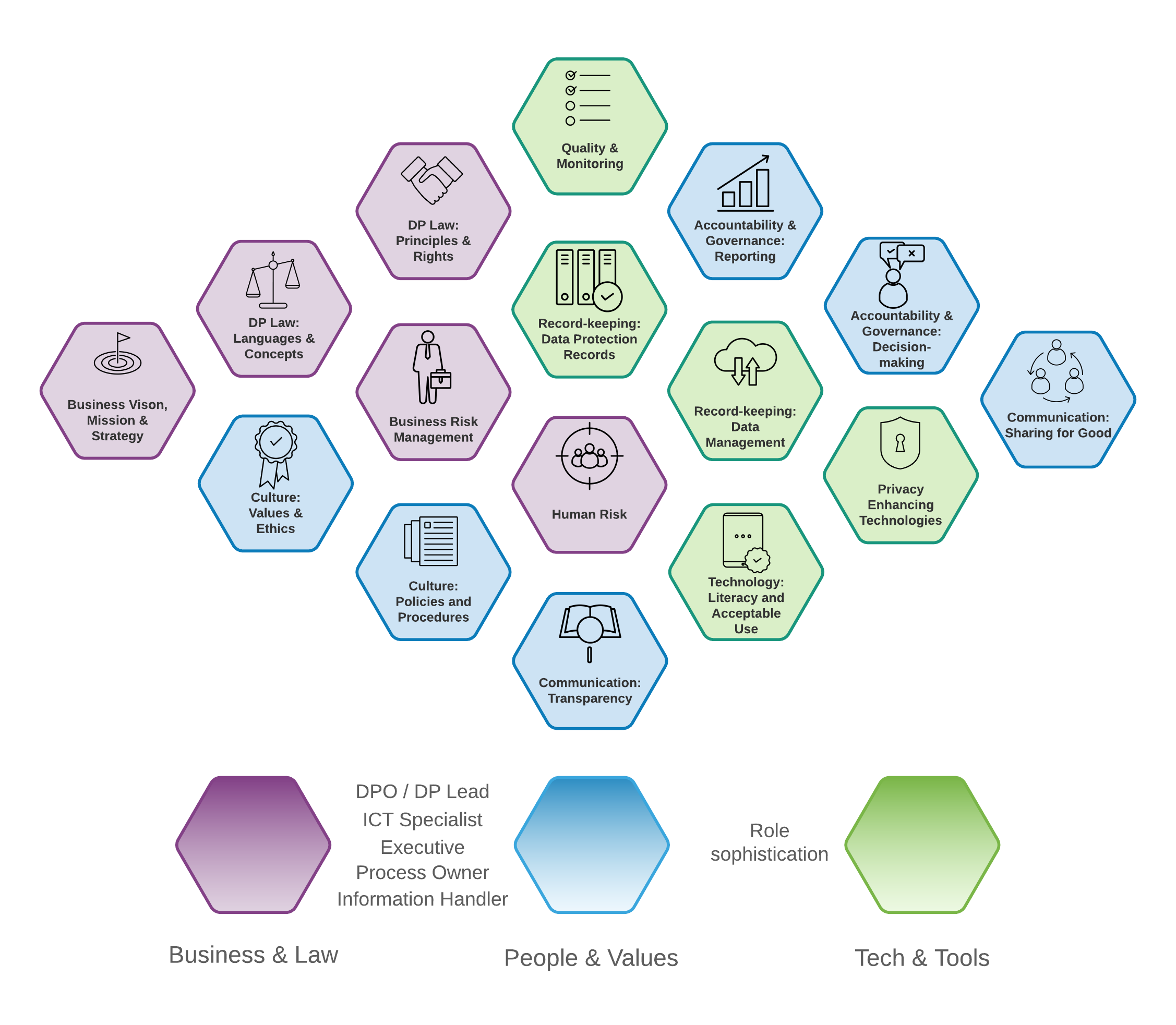
The framework is organised into three domains for data protection competency:
- Business & Law
- Technology and Tools
- People and Values
These cover all aspects of data protection practice and management that an organisation needs to consider.
Each domain has an area of practice, and within these areas are particular focus topics.
Every competency is defined by a “You” statement, which describes behaviour that relates to good practice in data protection. The "You" depends on your role in that process, but broadly, there is an increasing level of sophistication from Information Handler to DPO.
To be helpful, we’ve identified some ways in which the behaviour can be demonstrated and supported with evidence, however these should not be viewed as exhaustive or prescriptive. Organisations and individuals are free to add their own ideas for demonstrating and measuring these competencies.
Licence
This framework is provided under a ‘CC-BY-NC’ Creative Commons license type, which means that anyone is free to reuse, re-mix, adapt and build on the original content in any format or medium, but only for non-commercial purposes, and only as long as Data Protection Education Ltd and Miss IG Geek Ltd are credited for the original content.
About this framework
The purpose of this framework is to establish an initial, baseline set of competencies for data protection which are industry- and sector-neutral, so that it can be adopted "as is", without requiring significant effort to map the competencies to specific role titles or functions.
It describes behaviours that support compliance and good practice in data protection so that individuals can acquire and demonstrate their maturity in this area; and organisations can build training programmes and performance metrics that relate to practical, real-world actions.
There is no "one size fits all" approach to data protection, as so much of its decision-making and activities are dependent on an organisation’s approach to risk, ethics or regulation; so this framework is designed to support foundational compliance efforts without dictating how specific activities should be carried out.
The framework
Business and Law
|
Role |
Competency |
Suggestions for demonstrating this competency |
|
Info Handlers |
You recognise and promote the benefits of good practice in data protection; for your organisation, data subjects and wider society. |
|
|
Business Process Owners |
You play an active role in aligning business practices with data protection obligations. |
|
|
Executives |
You frame robust data protection practices as a strategic enabler when addressing your organisation’s compliance position and operational standards. |
|
|
DPO |
You advise on where and how good data protection practices can support the delivery of the organisation’s vision, mission and strategy. |
|
|
ICT |
You seek to align and balance conflicts of interest between ICT objectives and data protection compliance. |
|
Tech & Tools
|
Role |
Competency |
Suggestions for demonstrating this competency |
|
Info Handler |
You keep an eye out for potential data protection problems and resolve or escalate issues when you notice them. |
|
|
Business Process Owner |
You foster a fair and consistent approach to risk and problem reporting. |
|
|
Executives |
You seek to mitigate systemic factors which present barriers to data protection quality and compliance. |
|
|
DPO |
You use data protection monitoring and reporting as intelligence-gathering tools to help the organisation manage risk. |
|
|
ICT |
Where you provide ICT support and/or services for measurement, tracking and reporting of performance or quality; you do so without excessive surveillance or unwarranted intrusion on individual privacy. |
|
People and Values
|
Role |
Competency |
Suggestions for demonstrating this competency |
|
Info Handler |
You obtain advice from the DPO to inform your own decision-making, rather than expecting them to make decisions on your behalf. |
|
|
Business Process Owner |
You make decisions with data protection as a key aspect from the start, rather than attempting to add it on later. |
|
|
Executives |
You accept accountability for making business decisions that have data protection implications. |
|
|
DPO |
You balance your organisation’s support needs with your professional obligations, including the need to avoid conflicts of interest with your DPO role. |
|
|
ICT |
You consider the "bigger picture" of the organisation’s data protection obligations and goals when making ICT decisions. |
|
Contact us today with any questions or for a
Free Consultation
Call us with any questions
0800 0862018
or email us on
info@dataprotection.education